Jump To: Support > KB > NetManager > Proxy > Transparent
Transparent proxying (a.k.a. forcing everyone to use proxy)
Transparent proxying intercepts all HTTP requests on port 80 (and optionally HTTPS on port 443) that would otherwise pass through the NetManager to the Internet. It passes on the request to the local web-filter. There are couple of limitations:
- It is incompatible with proxy authentication
- The NetManager must be connected in-line so that it sees web traffic going out to the Internet. In practice, this usually means using NAT and having the NetManager connected directly to the router.
Direct attach, transparent proxying will NOT work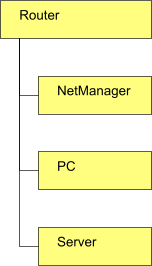 | In-line, transparent proxying WILL work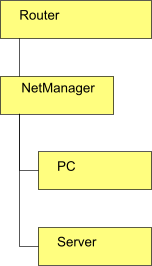 |
Enabling transparent proxying
You need to determine three things:
- Which network interface you want to intercept the traffic on (e.g. wm0)
- Which port number should be intercepted (generally 80 for HTTP and 443 for HTTPS)
- A free port for the web proxy to use (e.g. 3200)
Then create a line like the following in the NetManager configuration file:
nat_transparent="wm0:80:3200"
And then run build_server from the command line
Transparent proxying for HTTPS
To intercept and filter https (port 443), you should add a configuration such as:
nat_transparent="wm0:80:3200 wm0:443:3443"
You will also need to have enabled the NetManager to be a certificate authority. N.B. you must have an Internet connection that does not block direct HTTPS connections. By enabling transparent proxying for HTTPS, any upstream proxies you configure will be ignored for HTTPS traffic. This is because NetManager needs to be able to speak directly to the origin server on your clients' behalf to determine what sites are being accessed.
For further details on HTTPS interception, see here.
Fine-grained interception
nat_transparent is a space-separated list of interfaces and ports to intercept. Within each entry, the sections are colon separated. Minimal format is:
interface:port-to-intercept:port-to-deliver-to
Flags made be added as extra sections on the end. Currently supported flags are:
- src - comma-separated list of client IP addresses to intercept (with optional netmask)
- fwd - IP address to forward to (default is localhost)
e.g.
xennet0:80:3300:src=10.0.45.0/24 xennet0:443:3443:src=10.0.45.1,10.0.45.2
Caveats
If doing transparent HTTPS interception, you may find some sites (or parts of sites) fail to display correctly. You may see SSL related errors in the browser and the proxy logs show errors along the lines of the following:SECURITY ALERT: Host header forgery detected on ... (local IP does not match any domain IP)
This happens if the client computer is using different DNS servers from your NetManager. It is particularly prevalent if you use the public Google DNS servers (8.8.8.8 and 8.8.4.4); in this case it may even happen if used on both NetManager and clients. The problem occurs because the client looks up an IP address for the website, tries to connect (which is intercepted by NetManager) and then when NetManager tries to connect to the same website, it gets a different IP address.
For full details, see https://wiki.squid-cache.org/KnowledgeBase/HostHeaderForgery





