Jump To: Support > KB > NetManager > Passwords
Password Management
Password authentication on the NetManager is required for many services such as:
- FTP
- telnet
- ssh
- File sharing
- Proxy authentication
- Web page authentication
- Calendars
- Webadmin
If the NetManager is stand-alone, passwords will be checked against the local password file. This is one-way encrypted text file (offering easy backup and restoration without allowing passwords to be determined). If the password field in the file is empty, no password will be required (but many services will not allow login without a password being specified, e.g. imap, ftp.). Alternatively, the account can exist but have an invalid password field (just a *); this will not allow the user to log on at all unless they can be authenticated using a different method (e.g. see LDAP below).
NetManager passwords are changed by simply going to http://netmanager/pass/ from a webbrowser on your internal network. By default, if the NetManager is part of Active Directory, the password will be changed on Active Directory first and if this succeeds, then the new password will be forced on the NetManager. In this way, passwords are kept in sync between the two systems.
The behaviour of the password-changing page can be altered by going to Security > Passwords in webadmin (default Password Changing tab). Any combination of change on NetManager and change on Active Directory can be configured.
You may change passwords from the Console Menu by choosing option A Ongoing server administration and then choosing one of:
- R Change 'root' password
- N Change 'ncadmin' password
- O Change other passwords
This is probably the best method to alter the root and ncadmin passwords.
LDAP authentication
Alternatively, all passwords can be checked against Active Directory (technically LDAP) first. If this fails, it will fallback to the standard NetManager password check. This means that passwords can be changed using standard Windows mechanisms (such as Ctrl-Alt-Delete or through Active Directory Users and Computers). Note, this means that both the LDAP and NetManager passwords will work.
To enable LDAP authentication, go to Security > Passwords in webadmin and then choose the Authentication Method tab. You may alter the domain and directory servers to test against, by default they are the internal DNS domain and the server(s) configured when joining the domain.
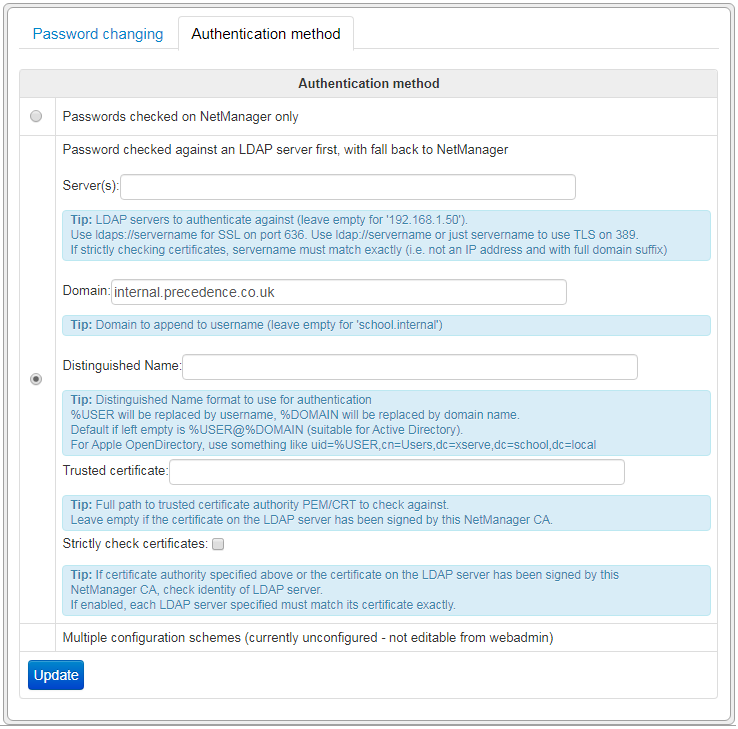
Certificate checking
The LDAP authentication will always try to connect to the LDAP server over an encrypted connection so that passwords are not sent in clear text. By default, it will use StartTLS on the standard LDAP port (389). However, LDAP-over-SSL port on port 636 is also supported if the server is specified with ldaps://.
When a secure connection is set up, the LDAP server will present a certificate which can be checked so NetManager can be certain the LDAP is genuine (and not a machine with the same name that is actually just collecting passwords). For the certificate to be checked, its issuer is checked against that of a trusted certificate authority (CA). The simplest way to implement this is to use the NetManager's inbuilt certificate authority feature to secure your Active Directory servers. Otherwise, you can specify the full filesystem path to the .crt or .pem file for the trusted CA. Once you have a properly signed certificate (either from NetManager or elsewhere), you can tick the Strictly check certificates box. Once enabled, if the certificate check fails access will be denied.
Advanced configuration
The authentication mechanisms used are controlled by setting authentication_type in the
NetManager configuration file. The default value is local which checks NetManager passwords only. Enabling LDAP authentication as above sets authentication_type to ldap. However, it is possible to achieve much finer control than this so, for example you can:
- Connect to other LDAP servers rather than Active Directory (e.g. Apple OpenDirectory)
- Alter the order of the mechanisms in which passwords are checked
To enable advanced mode, set authentication_type to multi. You may then define your own authentication schemes and specify the order in which they will be checked by listing them in authentication_schemes. The scheme local is always automatically defined, but you may choose whether to use it or not.
To define your own scheme, just give it a single-word name. You must then define the servers to use in authentication_servers_<SCHEME>, e.g. ldap://10.0.0.2 to do an LDAP connection to 10.0.0.2 (use ldaps:// for an SSL connection on port 636 otherwise StartTLS will be used on port 389). You may also define the name format to use when connecting to the LDAP server in authentication_dn_<SCHEME>; %USER will be replaced by current username and %DOMAIN by the Windows domain that the NetManager is joined to. If not specified the default is %USER@%DOMAIN (which is accepted by Active Directory).
You may optionally specify a list of users and groups that will use this scheme (this is based on NetManager groups) in authentication_users_<SCHEME>; groups are specified beginning with @. If you do not specify a list of users/groups, all users will use this scheme. For the local scheme this list will effectively specify which users will also have their password checked locally even if LDAP rejects the username/passwd.
If you do not specify local in your list of schemes, no local users passwords will be checked except for system users (i.e. users root, ncadmin and any others in group wheel).
For example:
authentication_type="multi" authentication_schemes="activedirectory opendirectory" authentication_servers_opendirectory="ldap://10.0.0.2" authentication_dn_opendirectory="uid=%USER,cn=Users,dc=open,dc=domain,dc=local" authentication_servers_activedirectory="ldaps://10.0.0.3" authentication_dn_activedirectory="%USER@%DOMAIN" authentication_users_activedirectory="@admin" authentication_strictcert_activedirectory="y"
This defines two authentication schemes: activedirectory and opendirectory. The two schemes have different servers and different username formats. Scheme activedirectory is checked before opendirectory, but only users in the NetManager group admin are checked against 'activedirectory. The certificate for Active Directory is checked for validity. The steps taken are:
- Is user in group wheel, e.g. root, ncadmin? If so, and password matches that on NetManager allow login
- If user in group admin? If so, and username/password is accepted by Active Directory and the certificate is correct, allow login
- Otherwise check username/password against Open Directory
- If username/password are not approved by Open Directory, reject the login
Add authentication_log="y" to log the steps taken during password checking to /var/log/messages.
Certificate checking can be configured globally or per-scheme. Set authentication_strictcert="y" to enable it globally (or when type is set to ldap). Use authentication_strictcert_<SCHEME>="y" to enable it for a specific scheme. If the NetManager has been used to sign the certificates on your domain controllers, then you do not need to specify a certificate to check against. Otherwise, use authentication_certificate="/full/path/to/certificate" to set it globally (or authentication_certificate_<SCHEME> to set per scheme).
External password changing
The web address http://netmanager/pass/ will only work internally on your network. If, after careful consideration, you want users to be able to change their password externally, you can use reverse proxying.
The following entry in the configuration file will make/pass/ available externally and will ensure this is only available over https:apache_reverse="/pass,http://127.0.0.1:880/pass,httpsredirect"
In the advanced use case where you have the majority of users on Active Directory, but a few on NetManager only (to ensure they have email access and nothing else), you can use the following:
apache_reverse="/pass,http://127.0.0.1:880/pass,httpsredirect /mailpass,http://127.0.0.1:880/pass/index.php/mode=local,httpsredirect"
In this case, if you go to /pass/, password changing will proceed as configured above (e.g. on Active Directory only). However, if you go to /mailpass/, password changing will happen on NetManager only.





