Proxy-HTTPSIntercept
Jump To: Support > KB > NetManager > Proxy > HTTPSIntercept
HTTPS inspection/interception
To intercept and filter https (port 443), you will need to have the HTTPS inspection module for your NetManager. If this module is installed, the proxy can monitor and decrypt HTTPS traffic that would normally be end-to-end encrypted between the client web-browser and the origin web-server.
The NetManager proxy can do HTTP inspection on transparently proxied ports as well as on explicit proxy ports that are set in your browser. For transparent proxying you should intercept port 443. For explicit proxying, you need to flag that the port should support HTTP inspection. To do this tick the HTTPS box on the Web proxy > Ports page in webadmin. Alternatively, you can add thessl flag to the port in the NetManager configuration file, e.g.squid_ports="8080 8083,ssl 8084"
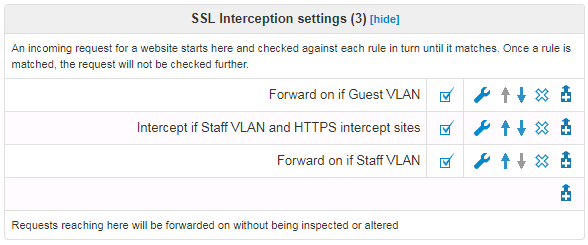
There are 3 operations that you can do with an intercepted HTTPS connection. You can configure these using normal proxy filters (except that you cannot use filters that require access to the raw HTTP such as URL path or User Agent)
- Forward on - connects the client to the origin server, but logs that the site has been accessed
- Block - terminates the connection which will give a browser error (not a friendly NetManager block page)
- Intercept - NetManager will decrypt the connection and log the encapsulated HTTP traffic. This allows you to block and log search engine queries, for example. To do this, you will need to install the NetManager CA cert as trusted on your clients.
For example: