Jump to CustomersLinton > Linton > Every
Every (WeAreEvery.com)
This is the compliance and HR system used by Anglian Learning. For integration with Office365 logins Every provide a 'headless' LDAP sync utility which submits data to the remote system, where an admin user has created mappings between AD groups and Every user roles.
LDAP mappings
- Login to https://www.every.education/ using the e-mail every@lvc.org and once on the first page click the
Adminlink in the left sidebar of the page - On the
User Administrationtab, and then underLDAP User Templatescreate anLDAP User Templatewhich maps between a template name and an actual Every permission level (e.g.IssuesOnly)
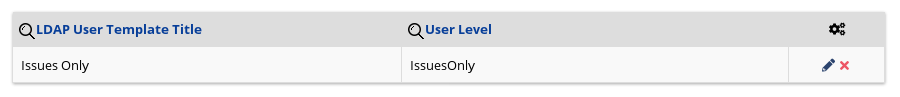
Note that required fields are marked and assigning remote groups is optional, so leave the User Group section blank.
- On the
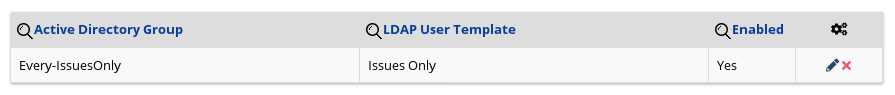
User Administrationtab, and then underManage Active Directory Mappingscreate a mapping between theLDAP User Templateand a named AD Group (i.e. a group name from your local AD instance which you will be using to sync Every settings)
Download sync utility
- Login to https://www.every.education/ using the e-mail every@lvc.org and once on the first page click the
Adminlink in the left sidebar of the page - Click the
Download LDAP (Headless)button at the top of the page - Save the download somewhere, but don't leave it lying around because the authorisation key to submit data is written into the archive
- Click the account name at the top of the screen, and then
My Account. Get/Set the username you will be using in the Task Scheduler, which must match the fieldWindows Account Name. The format isDOMAIN\Username. This is likely meant for use with SSO, but this is apparently how the data submission is referenced against the user.
Install sync utility
Inside the archive for the downloaded sync utility there are installation instructions, but they are poorly written and the setup it describes wouldn't work if taken literally (an admin user logged into a server who then never logs out). Admin rights aren't needed but the main problem is that not using an admin account requires Log on as a batch rights for whichever used is used.
The sync utility can only work from the Task Scheduler, since part of what it does it to look at the Task Scheduler for the task named Every.Ldap.Headless. It pulls the username from the task properties (either author or owner, I'm not sure which) instead of the security context of its own process. There is no configuration step, presumably it sends every user and every group.
- Create a GPO which will modify the
Log on as a batch jobfor the machine which will run the sync task, adding the default values as well as. The setting is located atLocal Policies/User Rights Assignment/Log on as a batch job, if the AD account used to sync will be namedeverysyncthe values are:- LINTON\everysync
- BUILTIN\Performance Log Users
- BUILTIN\Backup Operators
- BUILTIN\Administrators
- Extract the sync agent archive into
C:\Every - Modify the permissions on
C:\Every, removing inheritance, then the default permissions for standard users, then add modify permission for theLINTON\everysyncaccount
\\every\c$\every NT AUTHORITY\SYSTEM:(OI)(CI)(F)
BUILTIN\Administrators:(OI)(CI)(F)
LINTON\everysync:(OI)(CI)(M)
File permissions are very important here. The write permission is needed because the log file will be written into this directory. Default permissions at this location will allow domain users to see the authentication token
- Configure a Scheduled Task named
Every.Ldap.Headlessand configure it to runLdap.Headless.exe. It is probably safest to import this reference task, since this also defines that task author with the same username
<Task version="1.2" xmlns="http://schemas.microsoft.com/windows/2004/02/mit/task">
<RegistrationInfo>
<Date>2020-10-21T10:51:58.6539799</Date>
<Author>LINTON\everysync</Author>
</RegistrationInfo>
<Triggers>
<CalendarTrigger>
<StartBoundary>2020-10-21T04:32:00</StartBoundary>
<ExecutionTimeLimit>PT2H</ExecutionTimeLimit>
<Enabled>true</Enabled>
<ScheduleByDay>
<DaysInterval>1</DaysInterval>
</ScheduleByDay>
</CalendarTrigger>
</Triggers>
<Principals>
<Principal id="Author">
<UserId>LINTON\everysync</UserId>
<LogonType>Password</LogonType>
<RunLevel>LeastPrivilege</RunLevel>
</Principal>
</Principals>
<Settings>
<MultipleInstancesPolicy>IgnoreNew</MultipleInstancesPolicy>
<DisallowStartIfOnBatteries>false</DisallowStartIfOnBatteries>
<StopIfGoingOnBatteries>true</StopIfGoingOnBatteries>
<AllowHardTerminate>true</AllowHardTerminate>
<StartWhenAvailable>false</StartWhenAvailable>
<RunOnlyIfNetworkAvailable>false</RunOnlyIfNetworkAvailable>
<IdleSettings>
<StopOnIdleEnd>true</StopOnIdleEnd>
<RestartOnIdle>false</RestartOnIdle>
</IdleSettings>
<AllowStartOnDemand>true</AllowStartOnDemand>
<Enabled>true</Enabled>
<Hidden>false</Hidden>
<RunOnlyIfIdle>false</RunOnlyIfIdle>
<WakeToRun>false</WakeToRun>
<ExecutionTimeLimit>PT2H</ExecutionTimeLimit>
<Priority>7</Priority>
</Settings>
<Actions Context="Author">
<Exec>
<Command>C:\Every\Ldap.Headless.exe</Command>
</Exec>
</Actions>
</Task>
The agent and the Scheduled Task definition are currently stored in \\resources\itsupport$\Software\Every Headless LDAP.
At no point do you need to login as the everysync user, you only need to enter its password when saving the scheduled task.





